SSH
What is SSH?
SSH, also known as Secure Shell or Secure Socket Shell, is a network protocol that gives users, particularly system administrators, a secure way to access a computer over an unsecured network.
SSH also refers to the suite of utilities that implement the SSH protocol. Secure Shell provides strong password authentication and public key authentication, as well as encrypted data communications between two computers connecting over an open network, such as the internet.
In addition to providing strong encryption, SSH is widely used by network administrators to manage systems and applications remotely, enabling them to log in to another computer over a network, execute commands and move files from one computer to another.
How to use SSH In Ubuntu 18.04
Before the ssh installation, update the system.
sudo apt update -y
sudo apt-get install openssh-server
After installing SSH.
Check the status of ssh.
sudo systemctl status ssh
To stop ssh
sudo systemctl stop ssh.
To disable the SSH service to start during system boot run
sudo systemctl disable ssh.
To enable it again type:
sudo systemctl enable ssh.
Allow ssh if the ufw is active
sudo ufw allow ssh
Connecting to SSH Over Internet
ssh {user}@{host}
For example, connect to lennie user and ip is 10.10.9.74
ssh lennie@10.10.9.74
output
The authenticity of host '10.10.9.74 (10.10.9.74)' can't be established.
ECDSA key fingerprint is SHA256:xXyVGVy1l27TVcjIQj2kgTTmLYN6WCB93YJB3mAHLkA.
Are you sure you want to continue connecting (yes/no)? yes
lennie@10.10.9.74's password:
Set Up SSH Keys
Though SSH supports password-based authentication, it is generally recommended that you use SSH keys instead. SSH keys are a more secure method of logging into an SSH server, because they are not vulnerable to common brute-force password hacking attacks.
Generating an SSH key pair creates two long strings of characters: a public and a private key. The public key placed on any server, and then connect to the server using an SSH client that has access to the private key.
Creating key pair
To create on the local machine
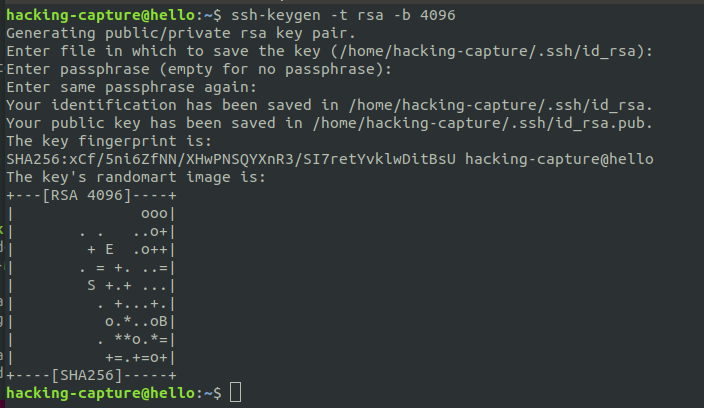
ssh-keygen -t rsa -b 4096
-t rsa : Specifies the type of key to create. The possible values are “rsa1” for protocol version 1 and “dsa”, “ecdsa”, “ed25519”, or “rsa” for protocol version 2.
-b 4096 : Specifies the number of bits in the key to create. The default bit number is 2048.
Specifying where the keys should be saved
Enter file in which to save the key (/home/hacking-capture/.ssh/id_rsa):
The default location for saving the files is the .ssh directory in the home directory.
Creating a Passphrase
SSH-keygen will ask you for a passphrase:
Enter passphrase (empty for no passphrase):
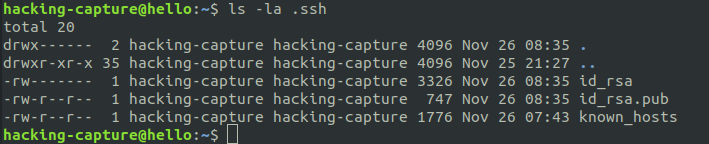
The keys pairs are located in /home/hacking-capture/.ssh/
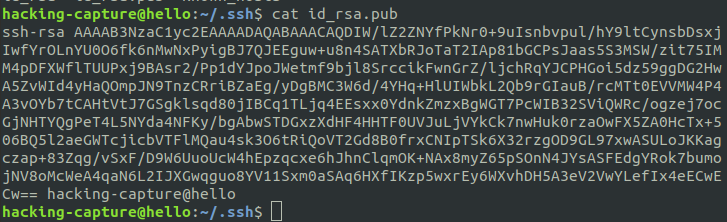
$HOME/.ssh/id_rsa– contains private key.
$HOME/.ssh/id_rsa.pub – contain public key.
Copying the Public Key to Your Server
Use ssh-copy-id command to copy your public key file. For example, $HOME/.ssh/id_rsa.pub) to on our machine on the remote server/host (lennie@10.10.9.74).
ssh-copy-id -i ~/.ssh/id_rsa lennie@10.10.9.74
-i identity_file, Selects a file from which the identity (private key) for public key authentication is read. The default is ~/.ssh/id_dsa, ~/.ssh/id_ecdsa, ~/.ssh/id_ed25519 and ~/.ssh/id_rsa.
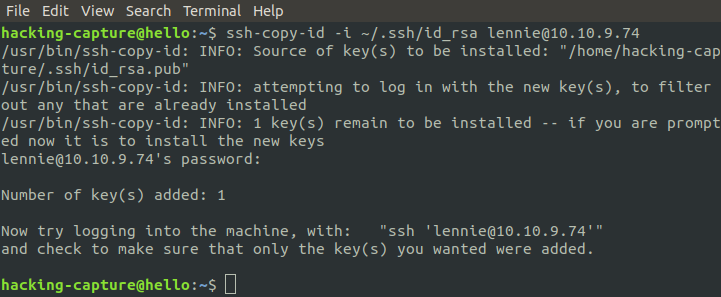
Let’s see if it work
ssh -i ~/.ssh/id_rsa lennie@10.10.9.74
-i identity_file, Selects a file from which the identity (private key) for public key authentication is read. The default is ~/.ssh/id_dsa, ~/.ssh/id_ecdsa, ~/.ssh/id_ed25519 and ~/.ssh/id_rsa.
Enter passphrase for key '/home/hacking-capture/.ssh/id_rsa':
Now login succussfully.